Sheltered Harbor was founded to protect customers, financial institutions, and public confidence in the financial system when a catastrophic event such as a cyberattack causes critical systems — including backups — to fail. Implementing Sheltered Harbor’s standards augments an institution’s disaster recovery and business continuity plans, with industry-developed crisis and emergency management processes. This enables institutions to proactively plan for and recover from crisis and continue to provide essential services for its customers while it reestablishes normal operations. Sheltered Harbor is a not-for-profit, industry-led “standards setting and certification” organization comprised of financial institutions, core service providers, national trade associations, alliance partners and solution providers dedicated to enhancing financial sector stability and resiliency.
Data Vaulting
Institutions back up critical data regularly in accordance with Sheltered Harbor standards, either managing their own vault or using a participating service provider. The data vault is encrypted, unchangeable, and completely separated from the institution’s infrastructure, including all backups.
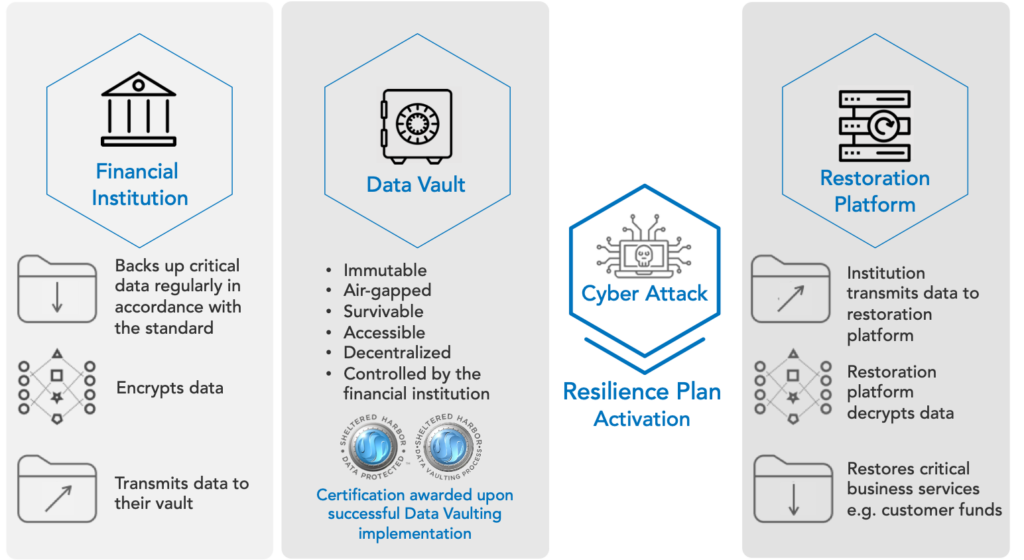
Resilience Planning
Sheltered Harbor participants must complete a rigorous and disciplined plan to address all business and technical steps necessary to restore essential services in the event of a cyberattack where all options to restore critical systems, including backups, cannot be completed in time to maintain customer confidence. Sheltered Harbor has defined specific playbooks that must be developed and tested by the institution before applying for and receiving Sheltered Harbor Cyber Resilience Certification.

Certification
Certification is a critical component of the Sheltered Harbor initiative. Participants adopt a robust set of prescribed safeguards and controls, which are independently audited for compliance with the Sheltered Harbor standard.
Upon completing the requirements, the institution will be awarded a Sheltered Harbor certification and an accompanying seal, communicating that their critical data is protected; or that they’re restoration platform is can be relied upon on the worst of days; or that their resilience plans are up to the task.
Data Protected
Data Vaulting Process
Resilience Plans




